C3's Multi-Layered Security Architecture

The digital landscape has seen immense change, and nothing more than security exemplifies this transformation. The shift from Web2 to Web3 made it clear that blending traditional exchange server security with an innovative trustless approach wasn't just smart but essential. And C3 was among the first to integrate this new approach into the platform.
C3 combined the best features of the two worlds. Instead of solely trusting the traditional exchange server security or the emerging trustless verification, we chose a blended approach. Combining the strengths of both paradigms has resulted in a robust security model.
An in-depth analysis of our system shows that with C3's strategy, many factors would need to be compromised for a setback to occur. In this article, we'll unpack this dual-security approach, shedding light on how we’ve merged the stability of Web2 with the trustless nature of Web3.

Web2 vs Web3 Security Fundamentals
Web2
Exchange server security mechanisms are well-understood and deeply ingrained in our digital infrastructure. They have been tried and tested, undergoing rigorous iterations to patch vulnerabilities and enhance their protective capabilities.
Think of HTTPS, SSL certificates, and firewalls. These technologies have guarded our digital spaces for years.
But exchange server security isn’t without its flaws. Centralization, a hallmark of Web2, not only introduces a major vulnerability point but also poses a risk, especially when such a system is responsible for custodying everyone's funds. A centralized system, if compromised, can cascade failures throughout the whole network.
Moreover, the dependence on intermediaries can sometimes slow down processes and add unnecessary complexities.
Web3
Web3 introduces groundbreaking concepts that distribute authority and trust, making applications less susceptible to single points of failure.
On top of that, with trustless verification, users have true ownership of their data and assets, presenting a paradigm shift in how we view digital rights and privacy.
But, like any nascent technology, everything that is trustless/decentralized has its problems (i.e. smart contracts). If audited incorrectly, they can harbor vulnerabilities leading to financial loss, data breaches, and eroded user trust. In fact, smart contract hacks and exploitations occur basically on a daily basis. While the decentralized nature of Web3 is a strength, it can pose challenges, especially in such an anarchic environment of internet, where everyone can attack and exploit the system anonymously.
C3's Security
Here at C3, we combined the reliability of exchange server security with the innovation of trustless systems. By doing so, we crafted a security architecture that is both resilient and fault tolerant.
Within the architectural framework of C3, traditional exchange server security mechanisms serve as the primary protective barrier, utilizing established and proven methodologies. If any issues or weaknesses bypass the primary security, a secondary decentralized layer comes into play.
The brilliance of this approach is clear: the odds of both systems failing simultaneously are low. With C3’s dual-security model, threats are confronted by multiple layers of defenses before they can cause any harm.
- Server-Side Layer
At C3, we understand and value the tried-and-true security foundations established by server-side technology. These mechanisms, matured over years of iterative enhancements, serve as the bedrock upon which we've built our robust security infrastructure.
- Uptime and Reliability
The Web2 paradigm emphasizes centralized servers and optimized routing, a structure that, when executed correctly, can offer unparalleled consistency and speed.
C3 has taken these principles to ensure that our services remain available and highly efficient.
- Risk Value
C3’s risk engine assigns a risk value to each user account portfolio. This value determines transaction approvals, like trading on margin or withdrawals, and defines liquidation approvals during price fluctuations.
What makes C3’s risk engine stand out is its capability to offer cross-margining, allowing all assets in a user’s portfolio to serve as collateral for trading. It has been battle-tested and modeled through all the extreme conditions the market has faced in the past. Furthermore, the engine employs conservative haircuts to ensure that the leverage in the platform never poses a systematic risk.
Apart from our off-chain risk engine housed in our server, we've taken an additional security step. We have implemented an independent risk engine on-chain that verifies health independently from the server. This engine utilizes the Pyth price oracle on-chain, adding a second independent validation layer for every margined operation, ensuring utmost security and reliability.
Web3 Layer
By integrating trustless verification mechanisms, we're not merely adding another layer of security, but actually leveraging the innovations of Web3 for which crypto users came in the first place.
- Decentralization
C3 operates on a trustless framework, ensuring that all operations are approved by the user’s private key and processed by smart contracts without any reliance on or trust in the server.
Every operation undergoes verification by the smart contract, which checks the signatures of the user's private keys and assesses the health of the accounts independently. This design ensures that the server holds no power to misappropriate user assets or act maliciously.
While the system is decentralized, it's crucial to note that only the server can interact with the smart contracts. This means that even if a potential vulnerability exists within the smart contract logic, it remains unexploitable unless the server itself is compromised. Thus, the system's design inherently protects against both internal and external threats, upholding the principles of decentralization and trustlessness.
- Self-Custody
Self-custody represents true ownership, giving users direct control over their assets without intermediaries. Holding their private keys, users ensure exclusive access, eliminating vulnerabilities tied to centralized entities. This approach offers unparalleled security and flexibility in how assets are managed.
At C3, we prioritize optionality, ensuring our platform is compatible with a wide range of technologies. This gives users the flexibility and full control over how they want to custody their assets. Whether you prefer a specific wallet or another custody solution, our platform is designed to accommodate your choice, granting you the comfort of selecting the best fit for your needs.
- Trust and Transparency
By settling every single operation in the blockchain, every action on our platform is traceable, verifiable, and immutable with transparent transaction histories. This isn't just a technical feature; it's a commitment to our users. Every transaction, every piece of data, is not only transparent but also fully auditable at all times, providing further safeguards and ensuring that everything stands up to scrutiny.
The Resulting Multi-Layered Security Architecture
We've taken a holistic approach to ensure that our users experience the highest level of security. The magic truly lies in our high-level architecture. Here's how the pieces fit together:
On-Chain Components
Our unified Smart Contract now handles a multitude of tasks. It oversees deposits and withdrawals; it's pivotal in liquidations, user balance management, and beyond. The Settler and Borrow & Lending functions are also integrated through this contract, ensuring valid transactions, precise order matches, and the secure oversight of borrowing and lending stances.
Additionally, our Account Delegation feature provides adaptability, letting accounts delegate tasks while always adhering to our stringent security protocols..
- Off-Chain Middleware
Security doesn't stop on-chain. Our off-chain middleware operates as an advanced validation layer. It conducts rigorous operation verifications, computes real-time health metrics, and efficiently handles order book matching algorithms.
- Interoperability
A standout feature in our multi-layered architecture is the ability of C3 to operate seamlessly with wallets across various blockchains.
By supporting popular signing algorithms such as ECDSA and EdDSA, we ensure compatibility not only with Ethereum and all EVMs but also with other chains like Solana, Algorand, and more.
The Practical Implications for Users
With our advanced security structure, we aim to provide peace of mind and a stable foundation for everyone involved.
For users, this means the following:
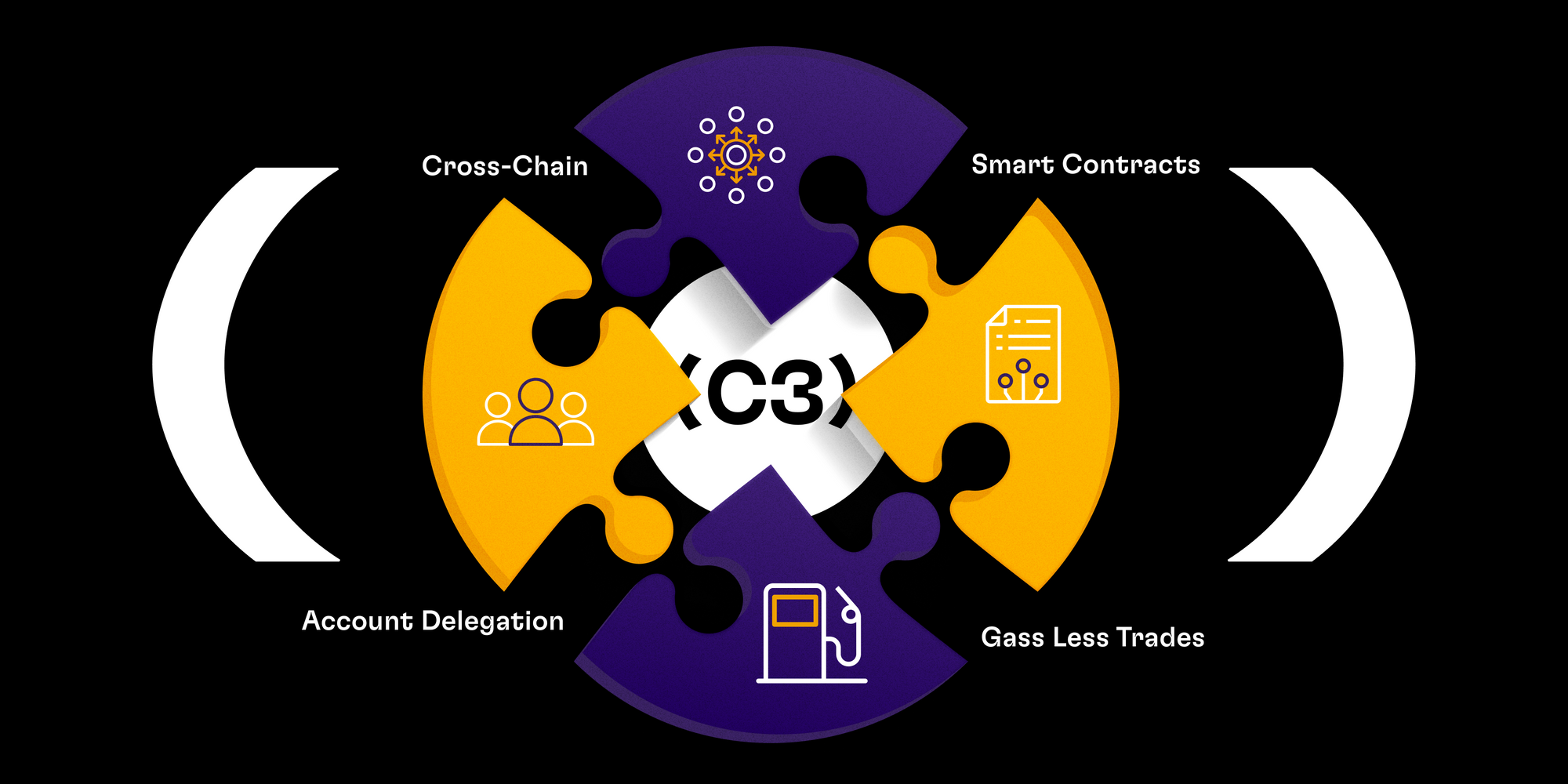
- Seamless cross-chain operations across the whole C3 ecosystem
- Our Smart Contract ensures that every action is precise and secure.
- With features like Account Delegation, you can delegate certain operations without compromising on security, giving you more freedom while ensuring safety.
- Operating C3 from Ethereum wallets enables a seamless, cohesive, and secure user experience, enhanced by gas-less trades and superior security measures.
The Bottom Line
By blending the best of exchange server security and trustless verification, we've built a solid multi-layer safety net for everyone who uses our platform.
Our main security goal is to keep every user and developer safe and confident. We've put a lot of effort into crafting it for you. As the technological landscape keeps evolving, with C3, you can be sure your assets’ protection are the top priority.
C3 Exchange – Your Gateway to the Future of Trading! To keep in touch, get announcements before everyone else, and participate in our community events, join our Twitter and Discord.
